
What is phishing?
Phishing is a type of social engineering where an attacker sends a fraudulent message designed to trick a human victim into revealing sensitive information to the attacker or to deploy malicious software, such as ransomware, on the victim’s infrastructure.
The most significant defence mechanism in phishing attacks is user awareness.
However, a more effective defence mechanism can be created with different defence layers. Adding controls such as e-mail filters, anti-spam, threat intelligence are the first steps towards achieving a more successful security posture.
While testing, phishing attempts that are blocked by layers other than the human vector mean nothing in phishing tests. The most important thing to test here is user awareness. It is inconvenient that organizations rely on spam filters and therefore do not care about user awareness.
I have observed that organizations typically have a 40% click rate during phishing simulations. Furthermore, 70% of clickers submit their login credentials or execute the malicious code on their computers.
Because we know that the click and success rates are drastically increasing with e-mails in the inbox, we have to be conscious about e-mails that bypass spam filters.
I want to talk about one of the spam bypass methods that I discovered while doing a phishing test, which has been successful for a long time: Flirting!
Let’s launch a phishing attack!
Let’s consider a scenario where we want to start with e-mail (Assuming we check a lot of factors such as DKIM, SPF, DMARC, domain categorization, etc. and get a healthy sender profile).
Let’s send the phishing e-mail:
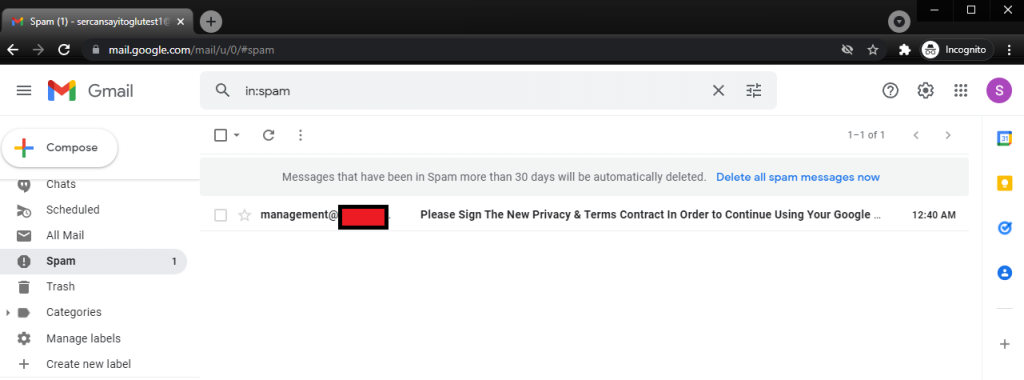
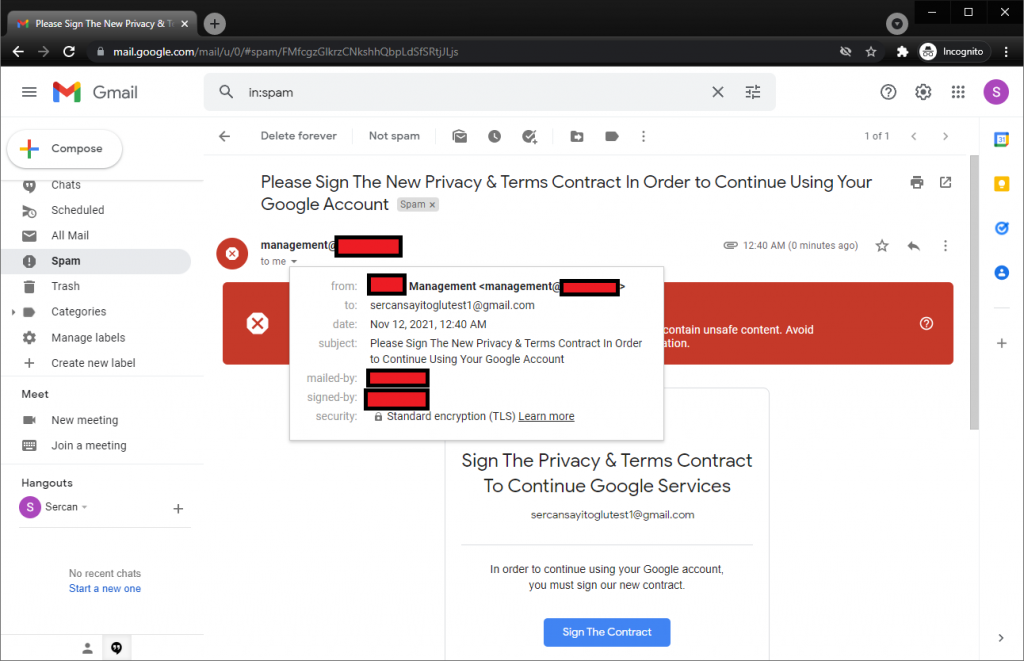
It has been caught by the spam filter, we can assume that it failed.
To mention a little bit of this phishing e-mail:
It is just a simple template with a link and HTML code. However, e-mails with links or documents are more likely to be caught by spam filters. Instead of sending such an e-mail in the first step, we should start with “flirting” via using a more appropriate e-mail.
Let’s try to send a simple e-mail without any links or documents to a new address:
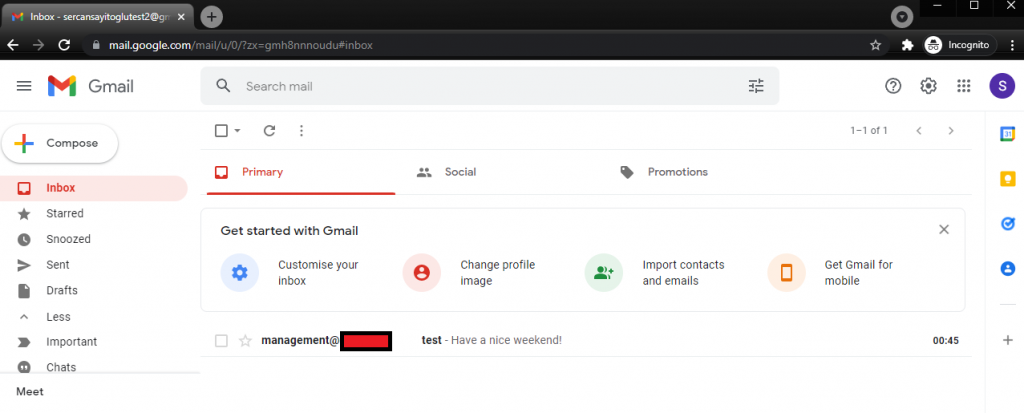
We can see that it is in the inbox.
Now let’s send our phishing e-mail:
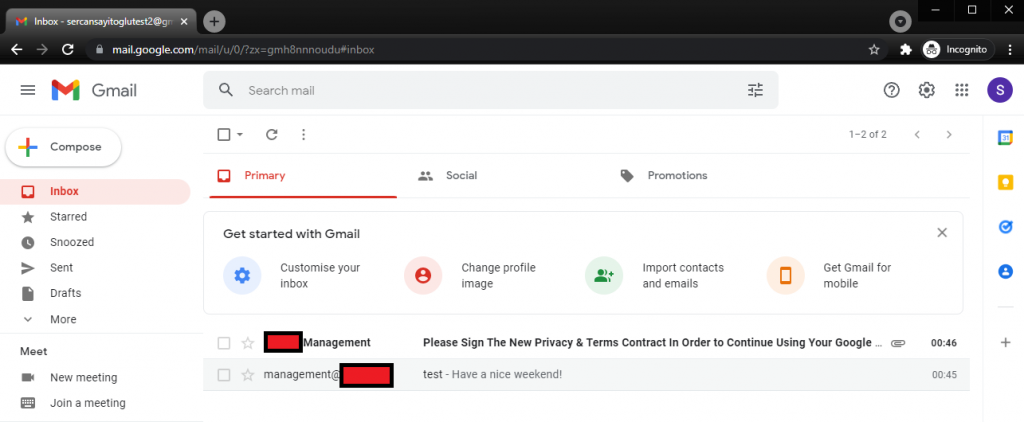
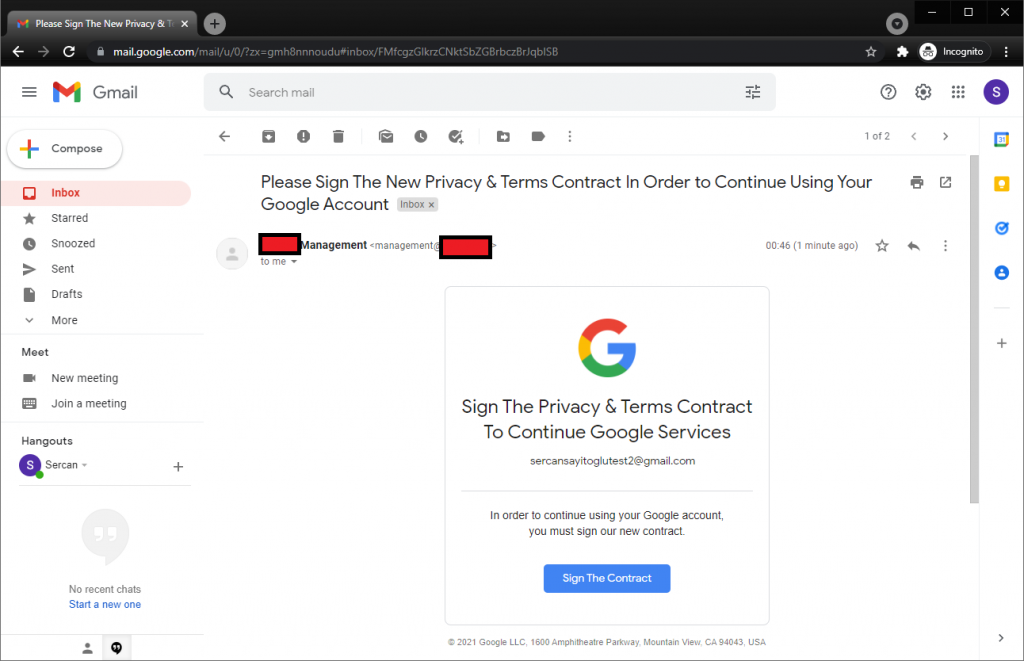
Excellent!
I guess we can call it the power of flirting 🙂
How does “flirting” as a spam filter bypass method work?
By sending a few innocent emails without links or attachments, we may have gained the confidence of spam filters.
It’s hard to get the same effect with a single innocent e-mail, so here are some other tricks to try:
- Sending more than one innocent e-mail
- Gradually increasing the complexity of the emails with harmless links or attachments after the initial message (For example appending this link: “https://policies.google.com/privacy”)
- The innocent e-mail and the e-mail with the link or document have the same title
Conclusion
We shouldn’t forget that there are no precautions that are impossible to bypass, therefore, it is recommended that organizations focus on continuous security testing and user awareness training.
