
Target: International Logistic Company
Access Point: External
Test Profile: Anonymous
I decided to spend my weekend with the bug bounty. I would like to talk about one of the vulnerabilities I have identified, which is quite striking.
I found a few wildcard records in the scope section. This encouraged me to devote time to the enumeration part. Thanks to the “Sia42” software, I was able to detect a lot of assets.
I found a lot of subdomains that belong to the target organization. After sorting out what was out of scope, I started to examine them.
Sometimes, sending an HTTP request directly to the corresponding IP address can tell us something about the target website.
When I checked the targets with their IP address, either a redirect response to a domain address was returned, or I was faced with a white blank page.
While looking at sites one by one to find logical vulnerabilities, I was aiming to detect simple vulnerabilities with “Hu42” automation software.
The lack of user login information made things difficult, but thanks to “Hu42” I found that the “.git” folder was accessible via using just the IP address instead of a domain name in the HTTP request.
Git
Git is software for tracking changes in any set of files, usually used for coordinating work among programmers collaboratively developing source code during software development. Its goals include speed, data integrity, and support for distributed, non-linear workflows.
“.git” Folder
The .git folder contains all the information that is necessary for the project in version control and all the information about commits, remote repository address, etc. All of them are present in this folder. It also contains a log that stores the commit history so that we can roll back to history.
When the .git folder is also deployed along with the web application, the attacker could exploit this misconfiguration to download the entire source code along with other sensitive data.
I used “Git Tools” to retrieve the files.
While reviewing the source code, I came across multiple certificates used for SSH, mail and HTTP protocol as well as valid FTP username and password.
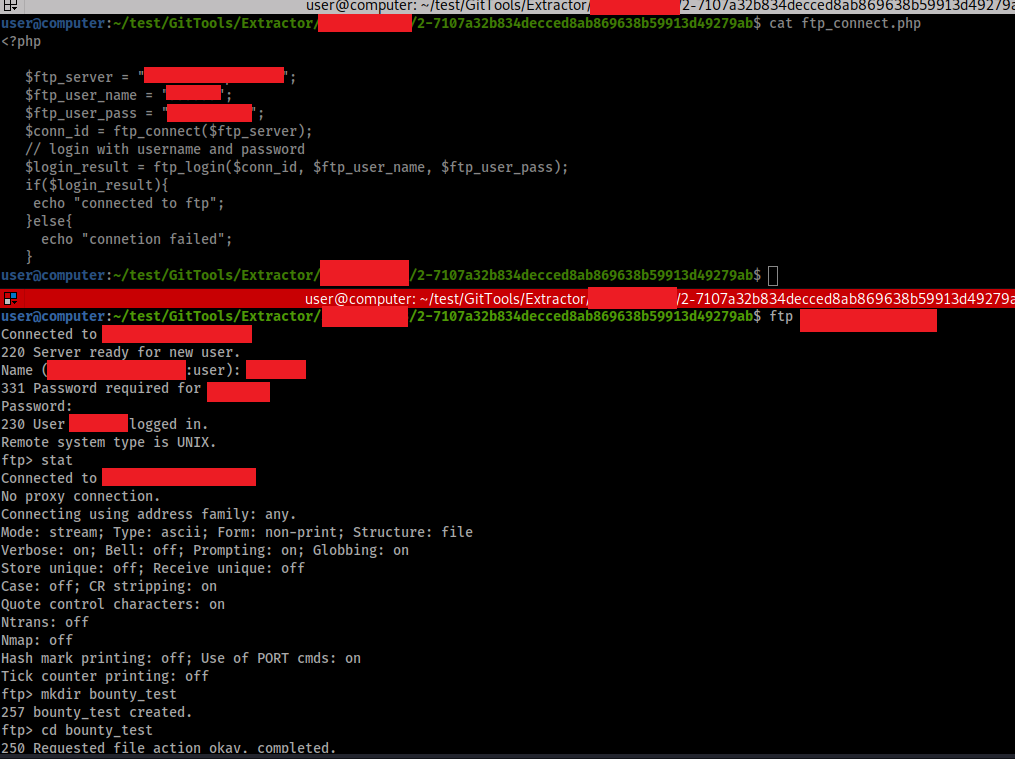

Going deeper was out of scope, so I chose to leave it at this point and report it. The effect of simple configuration mistakes on the security processes of organizations has also been proven.
I usually see analysts checking assets with the only version based vulnerability analyzer tools or simple testing tools to detect vulnerabilities and keep them secure. However, they forget how valuable the concept called enumeration and the valuable information that can be obtained from it.
