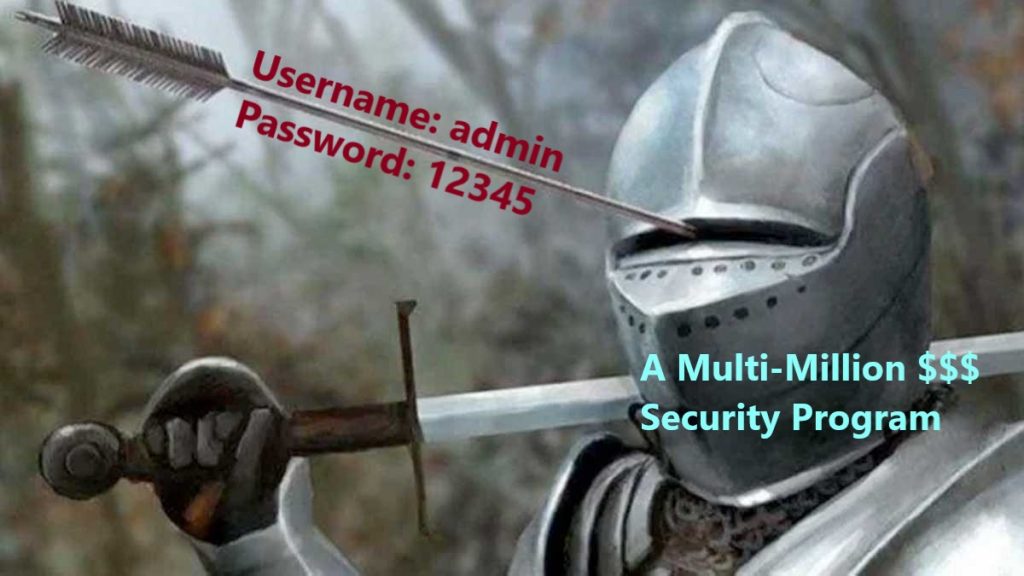
Real Life Pentest Scenarios #1 – Shortest Way To Domain Admin
I would like to share an incident that I encountered years ago, in a penetration testing project which can give a very good idea about how inconsistent the security maturity and self-confidence of institutions can be. I would also like to remind you that dozens of such events encountered every year. Target: International OrganizationAccess Point: […]
Real Life Pentest Scenarios #1 – Shortest Way To Domain Admin Read More »