In today’s fast-paced technology landscape, the importance of DevSecOps cannot be overstated. As organizations strive to deliver software faster and more efficiently, security has become an integral part of the development process. However, many companies still make common mistakes that compromise the security of their applications.
In this blog post, we’ll focus on the security aspect of DevSecOps and discuss common mistakes to avoid. From neglecting threat modeling to overreliance on automated tools, these mistakes can undermine your efforts to build a secure software development pipeline. By understanding these mistakes, you can take steps to prevent them and ensure that your DevSecOps process is as robust as possible.
Whether you’re just starting out with DevSecOps or looking to improve your existing process, this blog post will provide valuable insights and practical tips to help you avoid the most common security mistakes. So, let’s dive in and explore how to build a more secure DevSecOps pipeline.
Not prioritizing security in the DevOps process
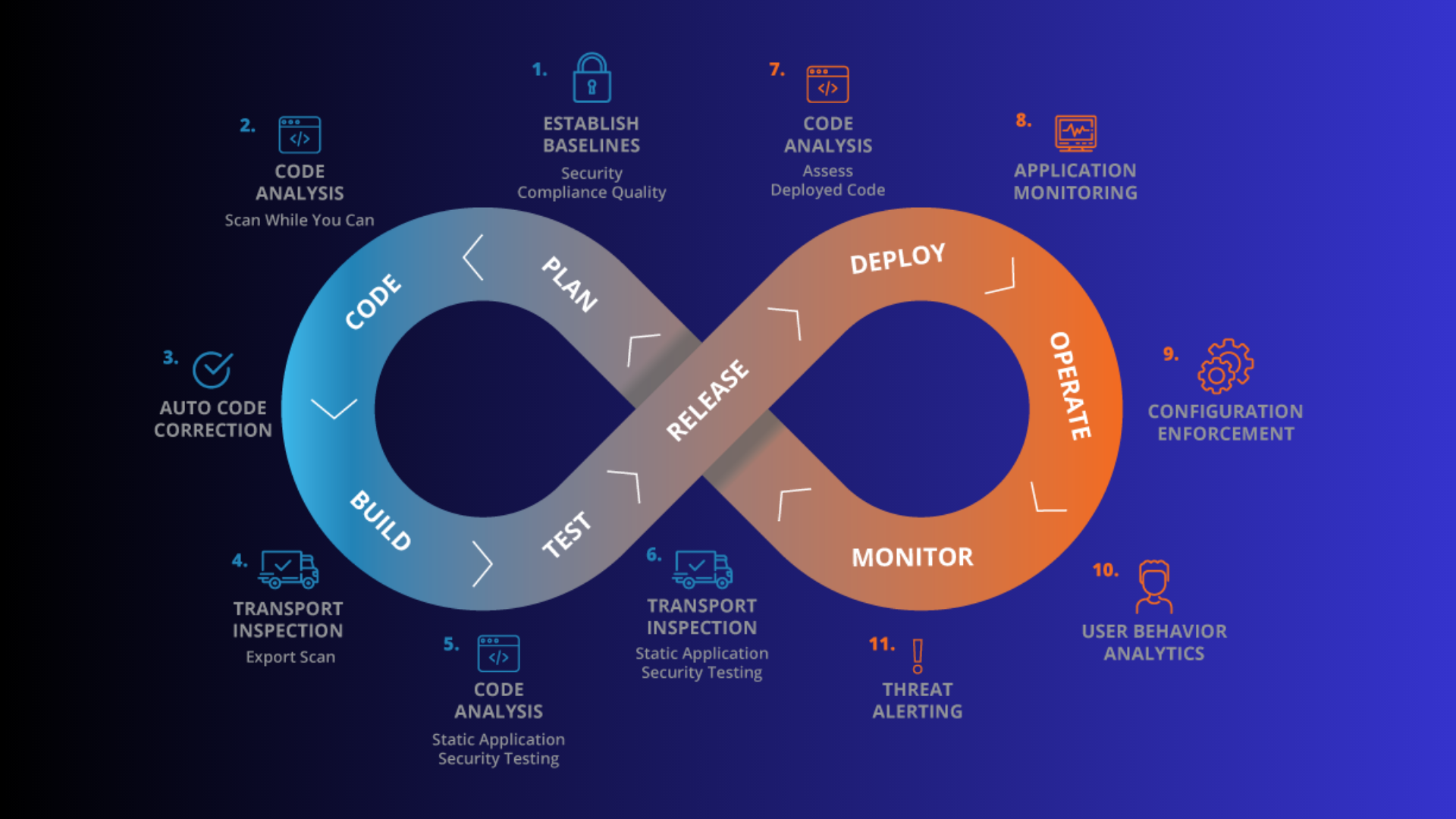
While it’s important to focus on speed and efficiency, neglecting security can have severe consequences, including data breaches and loss of reputation. That’s why it’s crucial to prioritize security from the very beginning of the development process and integrate it into every step of the pipeline.
To avoid this mistake, organizations should involve security experts from the outset and make security a top priority throughout the development process. This means conducting security assessments, implementing security controls, and testing for vulnerabilities at every stage of the pipeline. By making security a priority, organizations can ensure that their applications are as secure as possible and that they meet regulatory requirements.
Neglecting threat modeling
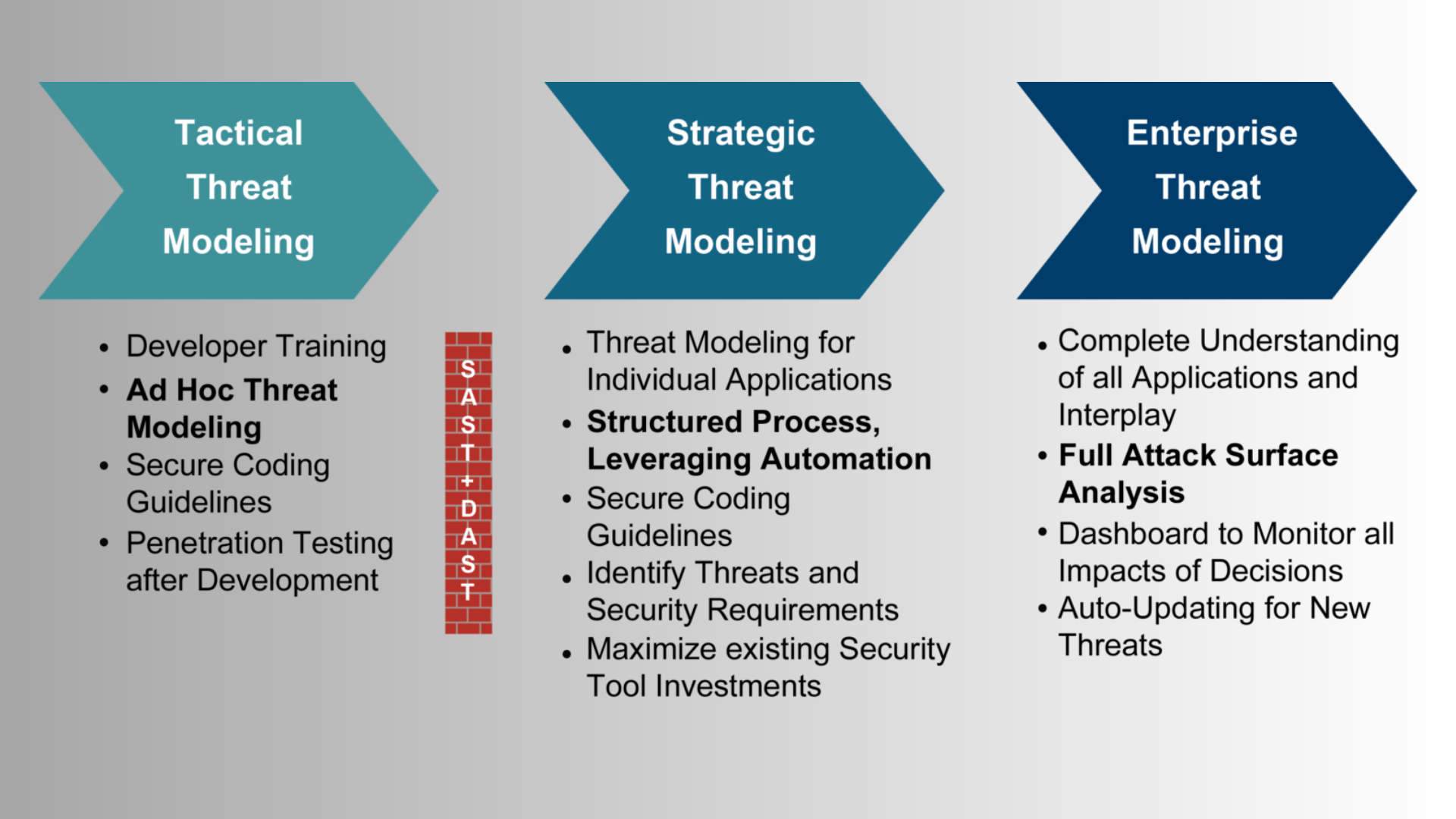
Threat modeling is a systematic approach to identifying potential security threats and vulnerabilities in an application. It helps developers and security teams understand the risks associated with their application and prioritize security measures accordingly.
To avoid neglecting threat modeling, organizations should conduct a threat modeling exercise early in the development process. This exercise should involve all stakeholders, including developers, security teams, and business analysts. By identifying potential threats and vulnerabilities early on, organizations can design security controls that mitigate those risks and prevent security incidents down the line.
Overreliance on automated tools
While automated tools can be useful in identifying security vulnerabilities and enforcing security policies, overreliance on them can be a common mistake in DevSecOps. Automated tools can only do so much and cannot replace the human element of security. This is especially true when it comes to more complex security issues or those that require context-specific analysis.
To avoid overreliance on automated tools, organizations should supplement them with manual testing and analysis. This means having skilled security professionals who can evaluate the results of automated tools, perform manual testing and analysis, and provide expert insights into the security of the application. It is important to recognize that every application has its unique characteristics and behaviors, requiring a customized approach to ensure its security. By using a combination of automated tools and human expertise, organizations can maximize their ability to identify and mitigate security vulnerabilities.
Failing to learn from past security incidents

Every security incident is an opportunity to learn and improve security processes, but organizations often overlook this opportunity. By failing to learn from past incidents, organizations risk repeating the same mistakes and leaving their applications vulnerable to similar attacks.
To avoid repeating the same mistakes in the future, organizations should conduct post-mortem analyses, and collect information about every security incident and discovered vulnerability in a centralized data pool. By categorizing incidents based on their root cause or other relevant factors, organizations can gain insights into the most common security threats they face. This information can then be used to plan investments and team trainings, so that organizations can eliminate the most pressing threats in the shortest time and minimum budget.
In addition to post-mortem analyses and centralized data collection, organizations can also leverage orchestration to streamline their security processes. Orchestration allows for the automation and coordination of security tasks, enabling teams to identify and respond to vulnerabilities faster and more efficiently.
By using orchestration tools to integrate security testing and analysis into the development process, organizations can identify and address vulnerabilities earlier in the development lifecycle, minimizing the risk of vulnerabilities making it into production. Additionally, orchestration can help teams to prioritize and manage vulnerabilities by collecting data from different sources and providing a centralized view of all vulnerabilities.
By collecting vulnerability data from different sources, including automated testing tools, manual testing, and incident response, organizations can gain a comprehensive view of their application’s security posture. This information can then be used to prioritize vulnerabilities based on their potential impact and the likelihood of exploitation, ensuring that the most critical vulnerabilities are addressed first.
Neglecting security culture and awareness

Even the most advanced security processes and tools are useless if employees and stakeholders don’t understand the importance of security and how to apply it in their work. Organizations must foster a security-first culture, where security is an integral part of everyone’s responsibilities and not just an afterthought. This requires ongoing security awareness training and communication, from the top down, to ensure everyone in the organization understands the risks and knows how to prevent them.
To avoid neglecting security culture and awareness, organizations must make security a top priority and allocate the necessary resources to ensure ongoing training and communication. This includes providing employees with regular security awareness training, emphasizing the importance of security in all aspects of their work, and empowering them to identify and report potential security risks. Additionally, organizations must encourage a culture of continuous improvement, where security processes are regularly reviewed and updated to reflect new threats and vulnerabilities.
Shouldn’t forget: Security is culture!
Not understanding the developer’s perspective

Developers play a crucial role in DevSecOps, and not understanding their perspective can lead to significant security gaps. Developers have unique insights into the code they write, and if they are not involved in the security process, they may inadvertently introduce vulnerabilities. To avoid this, organizations must ensure that developers are involved in the security process from the beginning and have access to the tools and resources they need to write secure code.
Security teams must understand how developers work and what they’re concerned about. By spending time with them and asking lots of questions, security teams can provide the information and support needed to make smart decisions at the right time.
To better understand the developer’s perspective, organizations must foster a culture of collaboration and communication between developers and security teams. This includes involving developers in threat modeling and vulnerability assessments, providing them with access to security training and resources, and soliciting their feedback on security processes and tools. By involving developers in the security process, organizations can ensure that security is integrated into the development process from the beginning and that secure code is produced as a result.
Failing to shift left
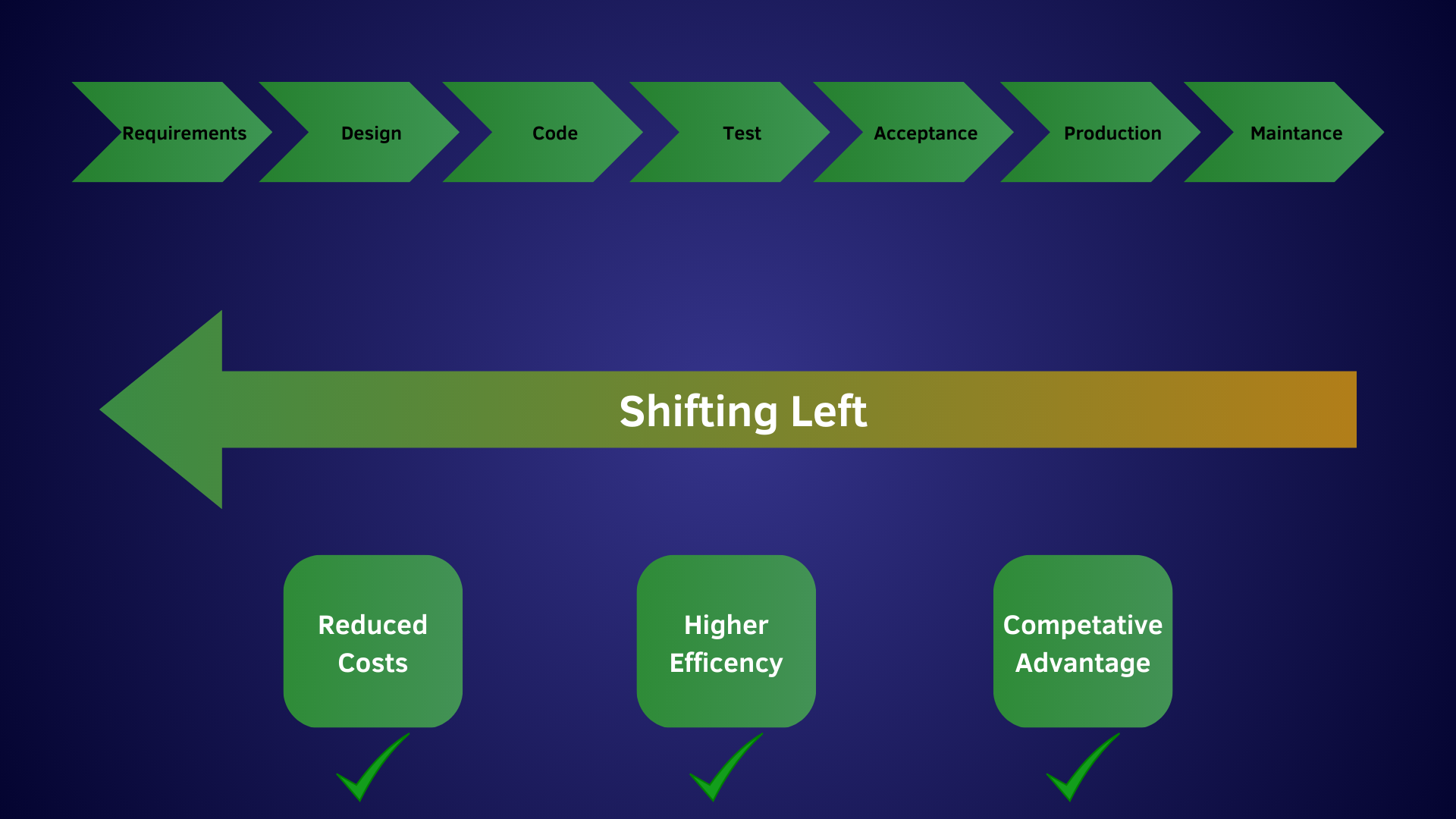
At first glance, the term “DevSecOps” might seem like just another acronym to add to an already lengthy list. However, its underlying philosophy assumes that you want to build a resilient and reliable system from the outset. DevSecOps is not just about adding security as an afterthought; it’s about integrating security practices into every stage of the development process.
One of the key principles of DevSecOps is shifting security left in the software development process. It means moving security activities earlier in the development process, rather than waiting until the end to test and fix vulnerabilities. By identifying and addressing security risks early on, organizations can reduce the likelihood of a successful cyber attack. Unfortunately, many organizations fail to shift left in security, and instead rely on reactive measures to address security issues. This can lead to delays in software delivery, increased costs, and even security breaches.
To shift left in security, organizations must prioritize security from the beginning of the software development process. This includes conducting threat modeling, performing code reviews, and integrating security testing into the continuous integration and delivery (CI/CD) pipeline. By doing so, organizations can identify and address security vulnerabilities early in the development process, before they become major issues.
Unrealistic goals and expectations

One common mistake in DevSecOps is setting unrealistic goals and expectations. This can happen when organizations try to implement too many security controls at once, or when they have unrealistic timelines for achieving security goals. In many cases, the development team is under pressure to deliver new features quickly, and security testing is often viewed as a hindrance to that process. This can lead to rushed and incomplete security tests, which can leave vulnerabilities undetected. Unrealistic goals can lead to frustration and burnout among team members, as well as a lack of progress in improving security.
To avoid setting unrealistic goals, organizations should prioritize their security initiatives and focus on the most critical security issues first. They should also set achievable timelines for implementing security controls and regularly review progress toward security goals. By taking a more strategic approach to security, organizations can avoid overwhelm and achieve meaningful improvements in their security posture.
Insufficient expertise with security tools

Many teams select tools that are not suitable for their specific use cases or fail to adequately train their team members to use them effectively. This lack of expertise can lead to security gaps or even exacerbate security issues. In some cases, teams may not even realize they are not using their tools properly until it is too late.
To avoid this mistake, it is essential to select tools that align with your team’s goals and expertise level. When implementing new tools, teams should provide thorough training and education to ensure everyone knows how to use them effectively. Additionally, ongoing education and training can help team members stay up to date with the latest security trends and best practices.
Failing with automation and continuous detection

Incorporating security into the continuous integration/continuous delivery (CI/CD) pipeline is also critical. This ensures that security testing is performed at every stage of the development process and that any vulnerabilities are identified and addressed as early as possible. CI/CD integrations enable automated security testing and provide real-time feedback to developers, allowing them to address vulnerabilities in a timely manner.
One of the key aspects of DevSecOps is continuous detection, which can help to detect security issues early on in the development process and afterward production stage. However, failing to properly implement and maintain these systems can result in significant gaps in security coverage. For example, relying on outdated or improperly configured scanning tools may result in false negatives, allowing vulnerabilities to go undetected.
Another common issue is failing to properly integrate automated security testing into the larger development process. This can lead to a lack of visibility into the security of the overall system, as well as missed opportunities to address vulnerabilities early on in the development process. It’s important to ensure that automated security testing is integrated into the larger development process and that it is designed to provide useful feedback to developers.
To address these issues, organizations should take a holistic approach to automation and continuous detection, which includes selecting the right tools and integrating them effectively into the larger development process. In addition, organizations should prioritize ongoing maintenance and monitoring of these systems to ensure that they are providing accurate and useful feedback to developers. By doing so, organizations can ensure that their DevSecOps processes are delivering on their promise of more secure, reliable software.
Failing to adapt and innovate in security goals

As technology evolves, so do the security threats that come with it. Focusing solely on traditional security goals without considering the changing landscape and emerging threats can lead to major security gaps. It is crucial to be open to new perspectives and innovative solutions that can address evolving security concerns.
One way to avoid this pitfall is to conduct regular security assessments and audits to identify potential security gaps and assess the effectiveness of existing security measures. This can help ensure that security goals are aligned with the evolving threat landscape.
Another way to stay adaptable is to prioritize ongoing education and training for both security and development teams. This can help them stay up to date on the latest security trends, tools, and techniques, and encourage a culture of continuous learning and improvement.
In conclusion, incorporating security into the DevOps process is essential for maintaining the integrity of any project. Neglecting any of the areas discussed above can result in significant security breaches that can lead to data theft, loss of customers, and damage to brand reputation. The best way to ensure that your DevOps team is equipped to handle security challenges is to adopt a culture of security awareness, continuous education, and a willingness to learn and adapt to new tools and processes.
By prioritizing security in the DevOps process, organizations can save time, money, and effort in the long run. Implementing secure coding practices, performing regular security testing, and integrating security into the development process from the beginning can help prevent the majority of security breaches. Additionally, understanding and respecting the perspectives of both developers and security professionals, and fostering open communication and collaboration between DevOps and SecOps teams, can help ensure that all aspects of security are addressed and incorporated into the overall project plan.
Ultimately, by taking a proactive approach to security, organizations can avoid costly security incidents and maintain their customers’ trust. Prioritizing security should not be an afterthought but a fundamental component of any DevOps process.
